In order for your emails to reach the inboxes of your subscribers, email providers such as Outlook, Gmail, Yahoo, etc. must be able to identify if your message is legitimate. A legitimate email means that it was sent by the owner of the domain name of the email address and not by a spammer.
Although domain authentication is an optional step, we recommend that you implement it. To accomplish this, you will need to implement these three protocols:
Why set up a domain authentication?
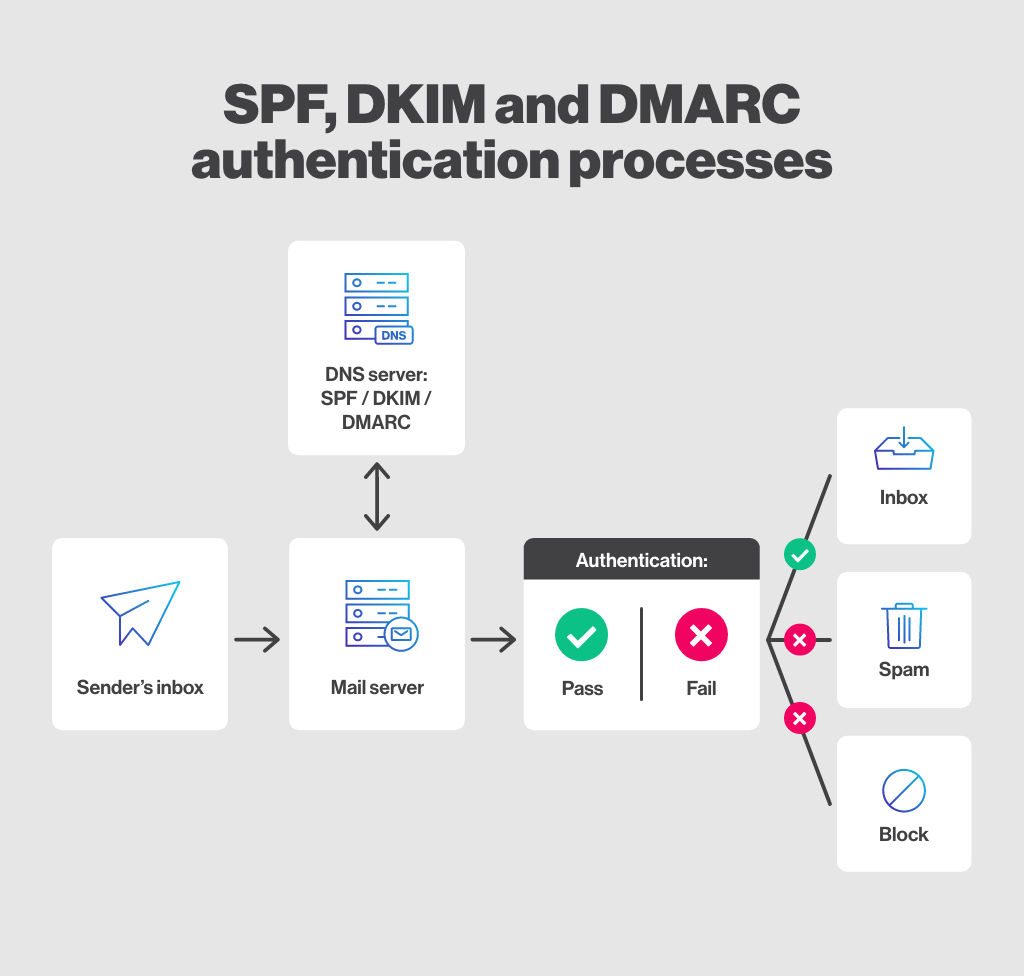
To apply a higher security level to your domain name:
Your readers will feel confident to open your emails since they will be able to see where your message is coming from and thus avoid the chances of opening a “phishing” email.
To strengthen your brand image:
While most recipients rely on the sender’s name and address to know from whom an email is sent, it is easy for a fraudster to impersonate your company without domain authentication and hope to get one of your customers or prospects to open a malicious email. This is a serious threat for companies that see their reputation destroyed in the eyes of the public.
To improve your deliverability rate:
By being identified as a legitimate sender, you are more likely to have your email reach your readers’ inboxes rather than falling into the “junk” folder. Note that this is not the only method to improve your deliverability rate, but it is one of many.
To comply with the regulations:
In some industries, domain authentication may be required by law or industry regulations. For example, Canada has the Personal Information Protection and Electronic Documents Act (PIPEDA).
In the United States, domain authentication may be required by law or industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Health Insurance Portability and Accountability Act (HIPAA).
What is the SPF protocol?
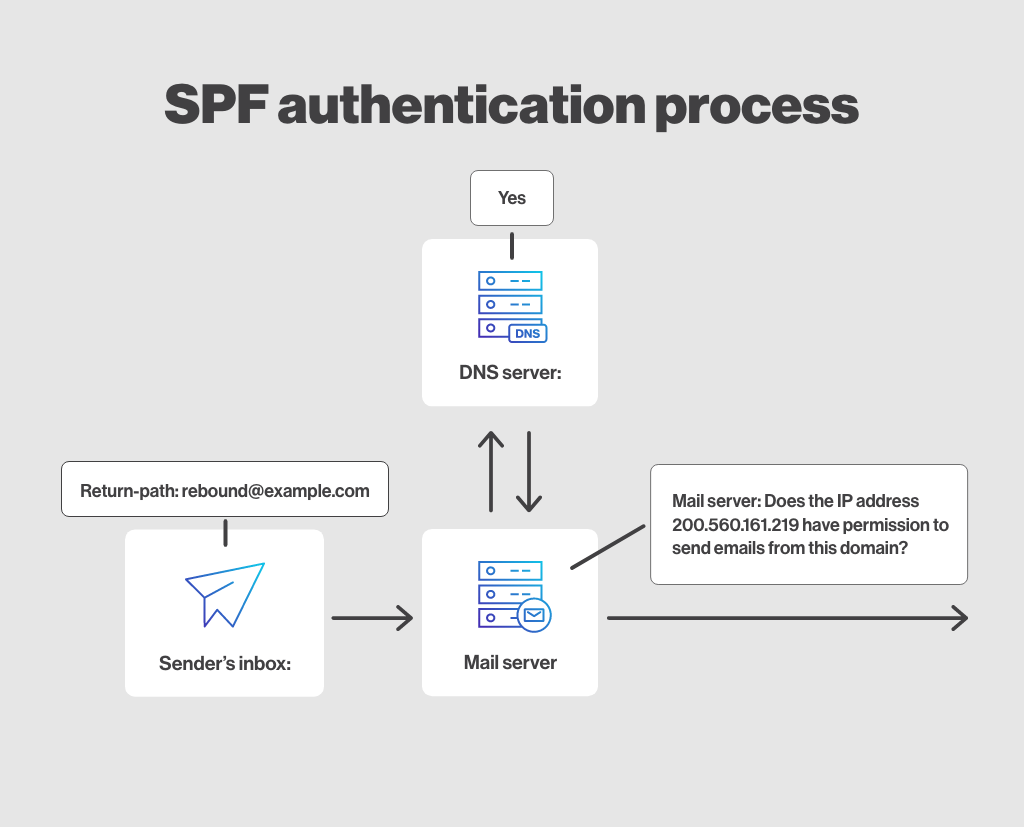
Sender Policy Framework (SPF) records allow your organization to manage who is allowed to use your domain name to send email. In other words, it allows the owner of a domain to publish a list of IP addresses or hostnames that are allowed to send email on their behalf.
When a recipient’s mail server receives an e-mail message, it can check the SPF record of the domain indicated in the “return-path” of the message to see if the server that sent the message is on the list of authorized servers. If the server is not on the list, the e-mail may be marked as spam.
The SPF protocol is implemented as a textual record in the Domain Name System (DNS) and can be used in conjunction with other email authentication methods, such as DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
What is the DKIM protocol?
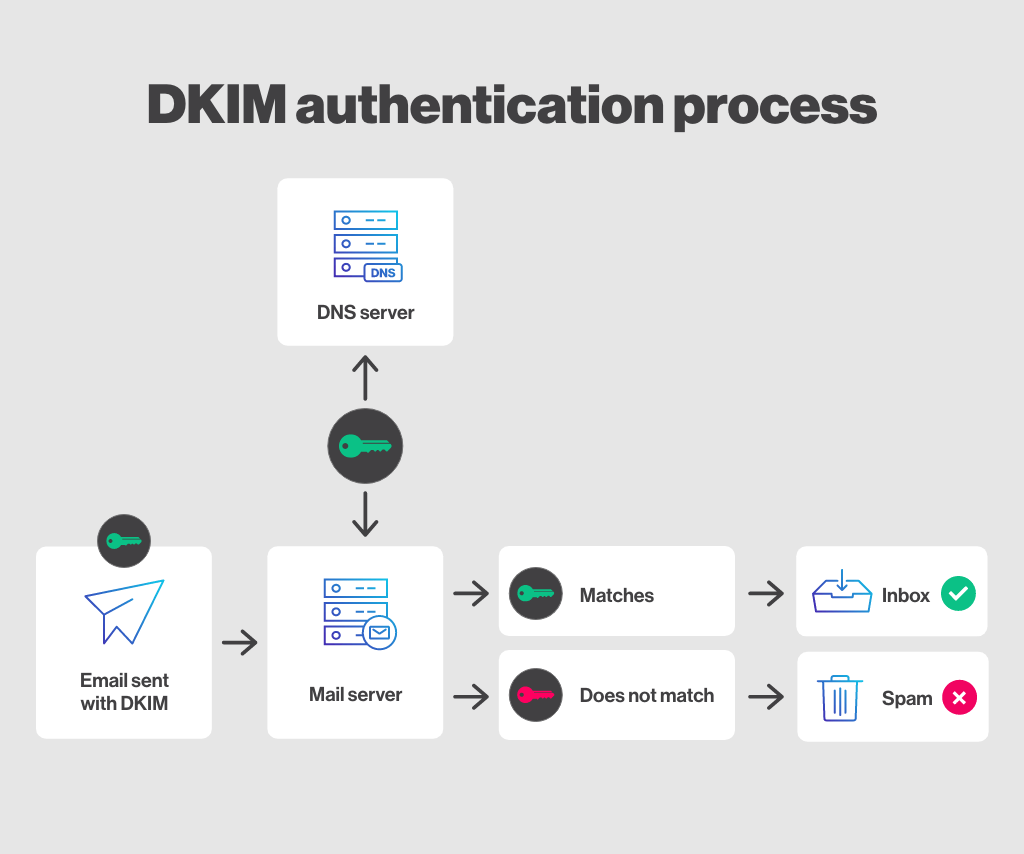
DomainKeys Identified Mail (DKIM) is an email authentication method that allows the person or organization sending an email to use a digital signature to associate the message with their domain.
This signature is included in the headers of an email message and is used to verify that the email was sent by the domain it claims to come from and that it was not altered in transit.
When a mail server receives a message with a DKIM signature, it can retrieve the sender’s public key from the DNS and use it to verify the signature. If the signature is valid, it indicates that the email was sent by an authorized sender and was not altered by a third party for the purpose of phishing.
DKIM is also a form of DNS record and is often used in conjunction with other email authentication methods, such as SPF and DMARC.
Note : Phishing is a type of online scam where a hacker sends out fake emails that appear to come from a legitimate company or individual, such as a company president. The goal is to steal sensitive information such as login credentials, financial information or personal data.
What is the DMARC protocol?
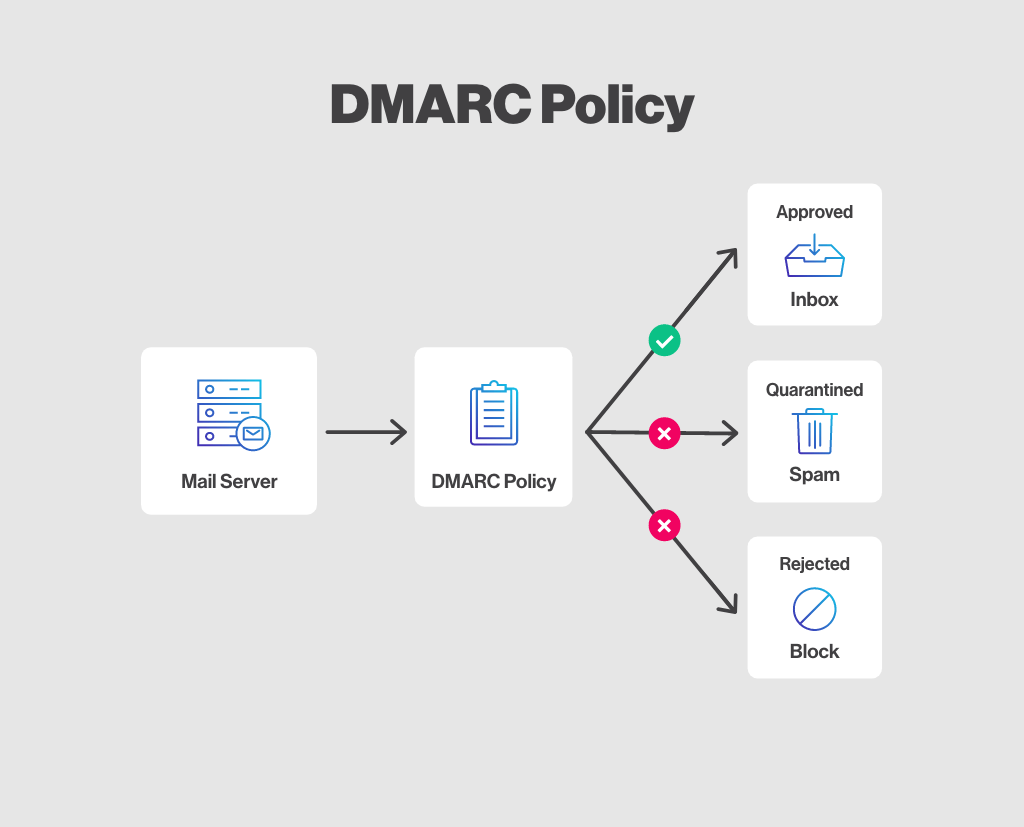
The DMARC protocol helps protect senders and recipients of email messages from spam, phishing and other forms of abuse. It works by allowing the owner of a domain to publish a policy in the DNS that specifies which mechanisms such as SPF and DKIM are used to authenticate email messages sent from that domain. For a DMARC to work, there are generally three elements that must be met:
- A passing SPF
- A valid DKIM
- Have an SPF or DKIM alignment*
Alignment:
SPF alignment: return-path domain is the same as the visible “FROM” domain.
DKIM alignment: DKIM signature domain is the same as the visible “FROM” domain.
In other words, when a mail server receives a message, it can check the DMARC policy for the domain specified in the “From” field of the message to see if the message has been authenticated using the specified mechanisms. If the message has not been authenticated, the server can take the following actions:
- Mark the message as spam
- Reject the email completely
- Do nothing if the email does not comply with the policy
DMARC also provides a mechanism for email receivers to report messages that pass or fail DMARC evaluation to domain owners. This allows domain owners to monitor the effectiveness of their DMARC implementation and identify any potential problems that would prevent a good email delivery rate.
Note : Cyberimpact offers an alignment with the DKIM signature.
Who is typically responsible for implementing SPF, DKIM and DMARC protocols for an organization?
Generally, it is up to the company or organization that owns the domain to set up the authentication protocols. However, your email service provider (ESP) can help you implement these email authentication methods.
How to implement SPF, DKIM and DMARC protocols?
To set up your DMARC, DKIM and SPF records, you will need to create the necessary DNS records and configure your mail server to use these authentication methods. Depending on your email service (ESP) and resources, you may be able to handle this process internally, otherwise you’ll need to enlist the help of a technical expert at your email service.
We recommend that you consult with your ESP or a technical expert to determine the best approach to implementing these email authentication methods for your organization. They will be able to advise you on the specific steps to take and help you resolve any issues that may arise.
How to configure authentication protocols with Cyberimpact?
DKIM :
All emails sent from our platform use a Cyberimpact DKIM signature by default. Cyberimpact’s DKIM signature has an excellent reputation and is sufficient for most senders. However, you can easily set up a DKIM for your domain if you wish, especially if you have a DMARC policy in place on your business domain name.
To get a personalized DKIM signature for your domain name :
- First, you will need to add an Alias (CNAME) in your DNS records to allow Cyberimpact to sign your emails leaving our platform with a valid DKIM key linked to your domain name.
- To do so, you must create the CNAME using the following nomenclature*: cyberimpact._domainkey.xxxxxxx | CNAME | clients._domainkey.email.cyberimpact.com
- The “x” must be replaced by your domain name, e.g. cyberimpact._domainkey.pizzasauce.com
- Once the CNAME is in place, contact our team so that we can activate the DKIM signature personalized to your domain name.
What is a CNAME ? A CNAME, or canonical name record, is a type of DNS record that maps an alias name to a true or canonical domain name. CNAME records are often used to point a subdomain to a domain hosting provider or to another subdomain.
SPF :
Cyberimpact automatically configures the SPF for all shipments made from its platform. Therefore, it is not necessary to create an SPF record or to modify an existing one to work with Cyberimpact.
However, if you wish to include Cyberimpact to your existing SPF record (even if it is not necessary), you just have to add “include:spf.cyberimpact.com” to it.
For example, if your current entry is :
v=spf1 include:spf.protection.outlook.com ~all.
You need to change it to :
v=spf1 include:spf.protection.outlook.com include:spf.cyberimpact.com ~all
What does Cyberimpact do to ensure good deliverability of your emails?
Cyberimpact makes sure to follow best practices to offer a good email deliverability to its clients thanks to several tools such as the use of an opt-in mailing list and the personalization of content that clients are encouraged to use. Cyberimpact also ensures compliance with data protection laws and spam regulations. Finally, all emails sent from its platform are well identified with an SPF and a DKIM signature linked to the Cyberimpact domain name.
However, it is important to note that compliance with SPF and DKIM policies does not 100% guarantee that the message will be delivered to the recipient’s inbox. This is because spam filters and email policies of email providers may block or move a message to the junk folder. Nevertheless, DMARC, DKIM and SPF authentication methods are still good practices for any company.
Conclusion
All of the above email authentication methods can help improve the deliverability of your emails. This way, you have a better chance of reaching your recipients’ inboxes than falling into your subscribers’ spam or being rejected.
If you have any questions about setting up your SPF, DKIM and DMARC with our platform, we invite you to contact Cyberimpact’s customer service.